We watched Howl’s Moving Castle tonight. I think it is one of my favorite Studio Ghibli movies. I think we’ve seen about half of the Miyazaki movies.

Day 4 without coffee and caffeine seemed to turn the corner. Felt a little less of a fog all day. Wasn’t tired all day. No headache today. I’ve felt more rested waking up the last two days. 🤞
POAP 7099088 at SPS - Sparky AI Launch!.

No Coffee?
I’ve been wondering how much caffeine is impacting me and yesterday, without much thinking about it, I decided to stop coffee for a while to see.
Today was day two without coffee. I had already cut back to just 2 cups a day for the last couple months but I still have felt super fuzzy and tired the last two days. I had a mild headache today and just felt slow. I’m hoping that I’m over the hump now. We’ll see.
My goal is to find out what benefits I may see to my blood pressure, sleep, anxiety, and who knows what else. The first two days have been more noticeable than I would have expected. 😬
Today I Learned: DNS and Wildcard Records
One of my favorite features of Fastmail is mail routing. I can use that to create any number of ad hoc email addresses in the format of anything at jamie.thingelstad.com. I’ve been using this feature for a while and to set it up you create a wildcard MX entry for your domain pointing to Fastmail. This way it works for all users of your domain. A couple of weeks ago these addresses stopped working though and I had no idea why.
I actually raised the issue with Fastmail support and they confirmed that there was no MX entry for jamie.thingelstad.com. They then asked if I had setup any CNAMEs or A records recently for that name. Then it hit me, I had recently created a TXT entry for jamie.thingelstad.com.
It turns out the second that there is any record of any type on a name you no longer get the benefit of the wildcard entry. I created the specific MX entries for jamie.thingelstad.com and everything started to work just as it should.
I just completed all the blog posts for our Milwaukee Spring Break trip. This is the most complete job I’ve done using daily logs (1, 2, 3, 4, 5), posts for most events, and a collection page linking to all posts as well as an index of all restaurants and attractions we visited.
We saw the New Standards perform tonight at the Dakota. It was a great show and featured a number of new and newer songs. Steve Roehm was on fire on the vibraphone tonight. 🔥

Happy Easter! We had family to Magic Pines and had a 90 Easter Egg Hunt outside looking for treats! It seems that only Mazie got the memo on dressing in brighter colors. 🐰


My friend @Bricker is lighting up his blog timeline with a bunch of new and old blog posts. Worth adding to your feed reader or timeline of choice. 🔥
I’ve been a fan of the IndieWeb community for years, but finally decided I should get a bit more active. I created my profile on the IndieWeb wiki, started as a backer, and signed up to host the next available IndieWeb Blog Carnival in April 2025.
Milwaukee Spring Break: Day 5
- Coffee and pastries at Pilcrow Coffee.
- Visit to the Milwaukee Domes after it was closed yesterday. Completed all of our stops! ✅
- 9:37a Depart Milwaukee for home.
- Stop at Culver’s in Tomah, Wisconsin.
- 3:14p Arrive at home.
Milwaukee Domes
We made a last minute final stop at the Milwaukee Domes before we left town. The tropical and desert domes were relaxing and pretty to experience.







Part of the Milwaukee Spring Break collection.
Beautiful and tasty Cortado at Pilcrow Coffee on our final morning in Milwaukee.

Part of the Milwaukee Spring Break collection.
Milwaukee Spring Break: Day 4
- Jamie has morning coffee at Discourse Coffee and today Mazie joined as well.
- Brunch at Uncle Wolfie’s Breakfast Tavern. Mazie and Jamie have Ube.
- Visit Harley-Davidson Museum.
- Attempted to visit Milwaukee Domes but they were closed.
- Explore Milwaukee’s Historic Third Ward.
- Saw Call Me Dancer at Oriental Theatre.
- Escaped “Invasion” room at 60 to Escape.
- Drop off car at hotel.
- Walk to San Giorgio Pizzeria for delicious pizza.

This is as close as we were able to get to the domes — closed on Tuesdays.
We had a great time escaping the “Invasion” room at 60 to Escape! The room was fun, surprising, and appropriately challenging. One of the best rooms we’ve done! Finished with 5m 37s remaining. Room 55!

Part of the Milwaukee Spring Break collection.
We saw Call Me Dancer at the Oriental Theatre while in Milwaukee. The movie told the story of Manish and his passion to become a professional dancer against many odds.

Part of the Milwaukee Spring Break collection.
Harley-Davidson Museum
We visited the Harley-Davidson Museum while in Milwaukee. None of us are huge motorcycle fans but it was still fun to see the history and progression of all the bikes over the years.
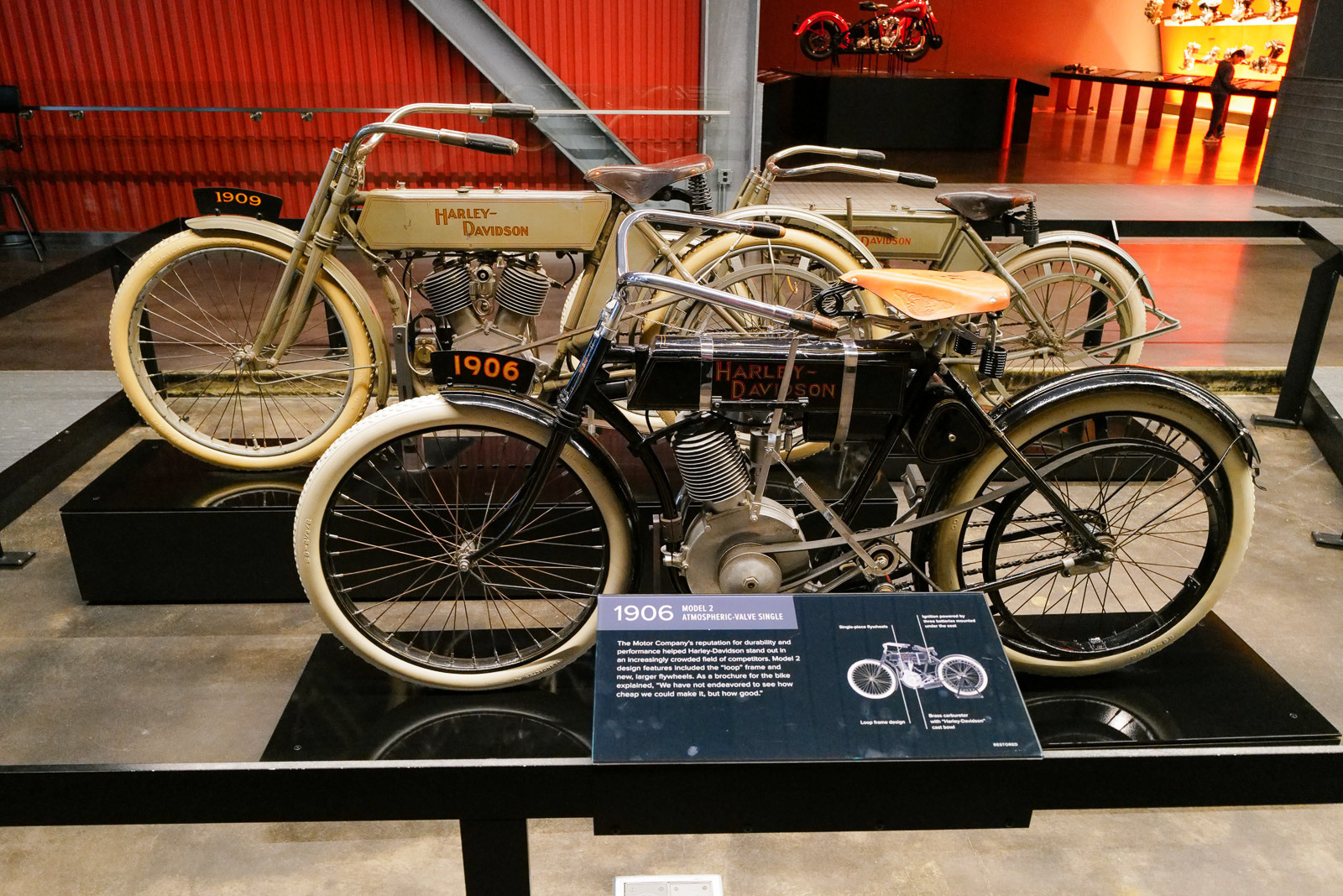
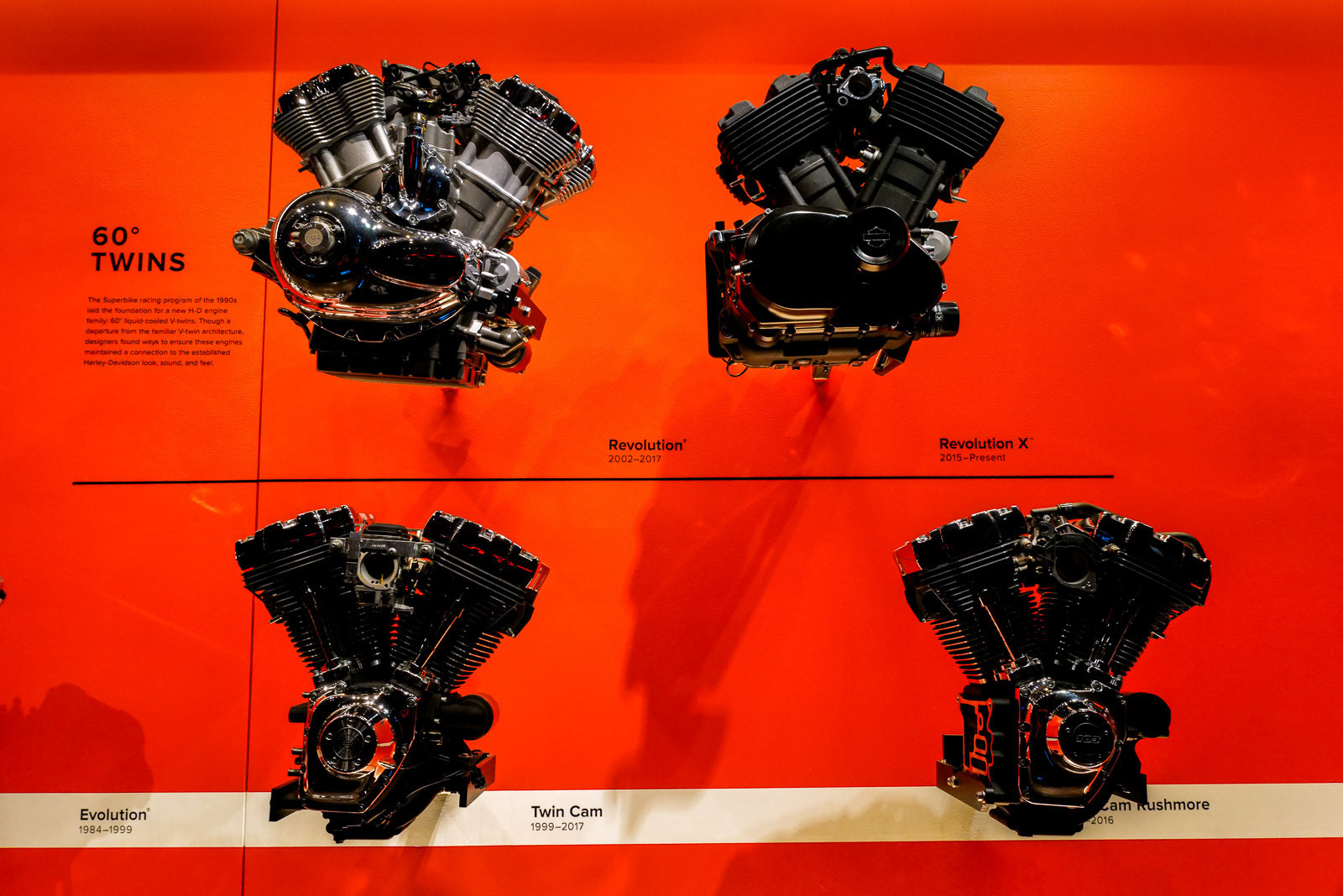
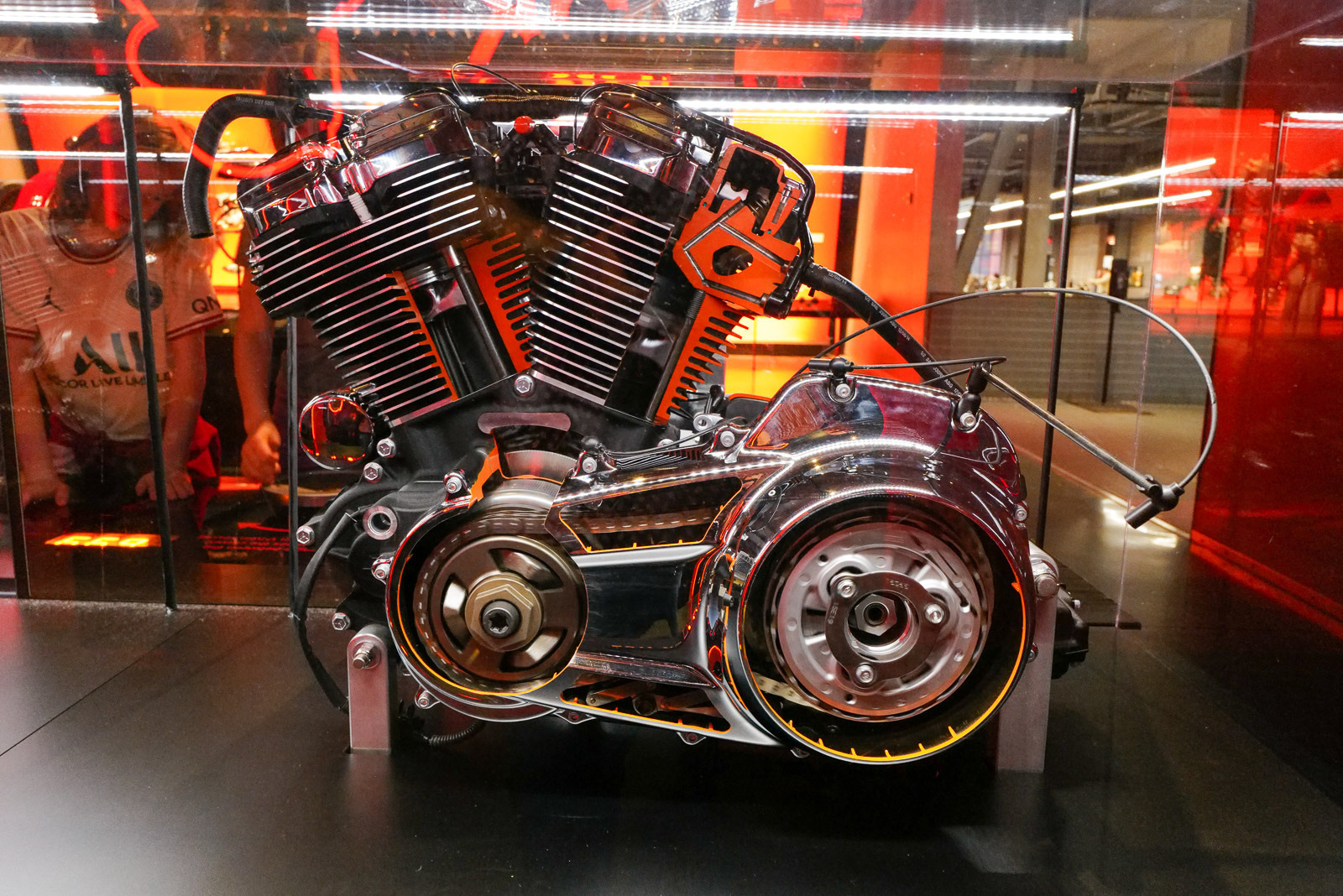
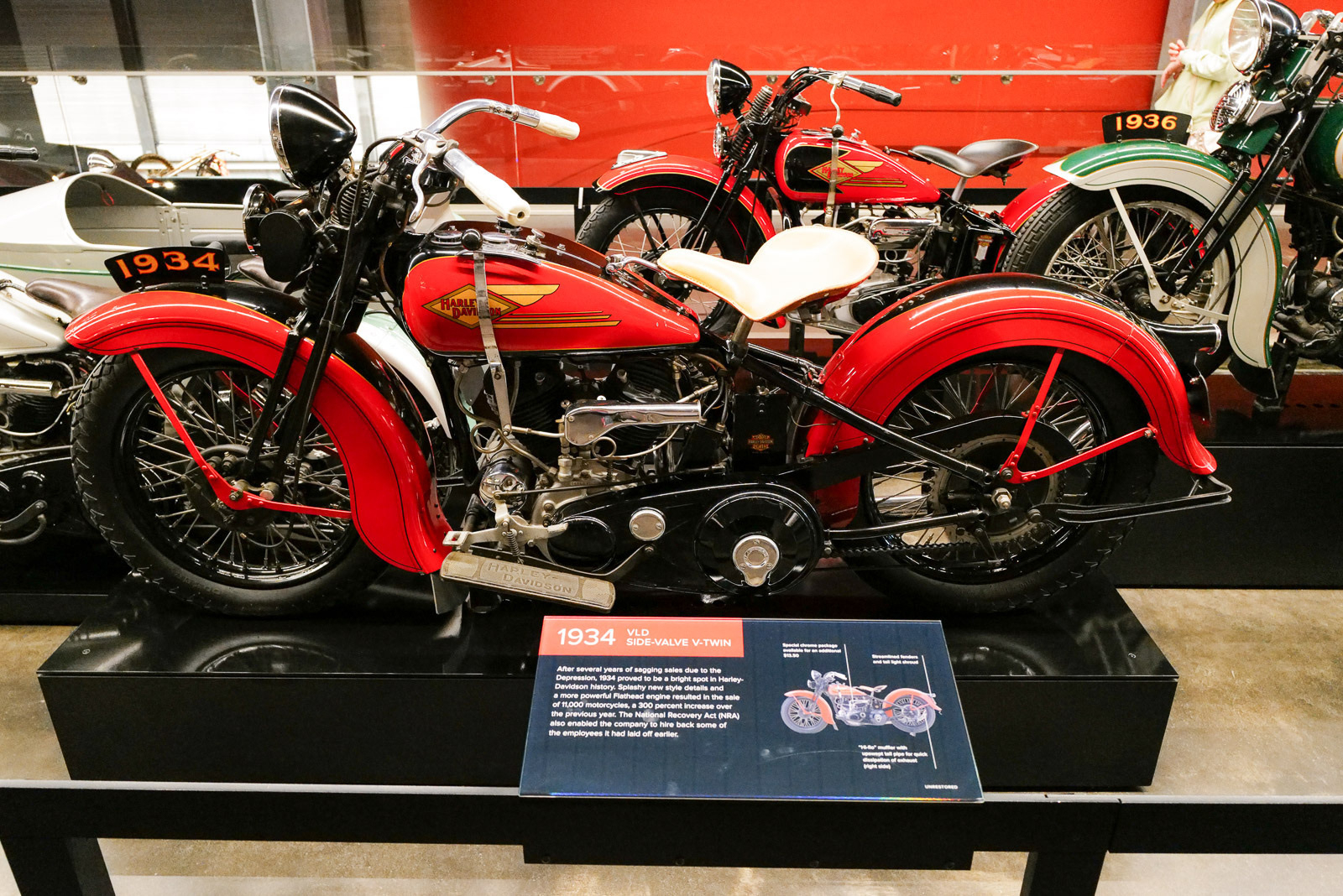






Part of the Milwaukee Spring Break collection.
The Ube Toast Crunch Oatmeal at Uncle Wolfie’s Breakfast Tavern is delicious and strikingly purple!

Part of the Milwaukee Spring Break collection.
While waiting for our table at Uncle Wolfie’s Mazie found these stairs and got some exercise. Then Tyler caught wind and a race was required.


Part of the Milwaukee Spring Break collection.
Return visit to Discourse Coffee this morning for a Moonwater (espresso, milk, honey, cinnamon, tellicherry black pepper, and applewood smoked sea salt). Yum. ☕️

Part of the Milwaukee Spring Break collection.